It’s challenging to go a few days without learning about a massive data breach that might expose millions of consumers’ sensitive information to hackers. You may safeguard your data from those you don’t want to share it with by implementing a few easy modifications to your devices and accounts. It’s simple to get started. Here’s a rundown of a few measures that can be taken to safeguard yourself and your data online.
Make it very hard for others to obtain credit in your name –One of the consequences of data theft is that someone takes out loans or credit cards in your name and then never pays them back. You might not find out until you’re ready to purchase a car or a house, at which point your credit could be wrecked. According to credit bureaus, there are three ways to protect yourself from this. To begin with, a fraud alert indicates that a lender must confirm your identity before issuing credit. Fraud alerts are free for the first 90 days, but they must be reactivated every 90 days. A credit freeze, on the other hand, prevents third parties from viewing your credit record. A criminal can’t get a loan or a credit card in your name if a lending institution can’t retrieve your credit report.

There may be charges associated with setting freezes, and if you intend to apply for credit later, you’ll have to request the credit bureau to remove the freeze. Finally, a credit lock is identical to a freeze, except that it can be lifted digitally. There may be fees associated with credit locks. Lenders have the option of checking one or all of the credit bureaus.
Here’s how you can ensure data protection online.
Install and keep antivirus software up to date
Antivirus software is what we call it, yet defending against real computer viruses is only a minor part of what it does. Ransomware encrypts your data (and thus provides data protection) and demands money in exchange for its recovery. Trojan horse applications appear to be legitimate apps, but they collect your personal information behind the scenes. Bots convert your computer into a zombie army soldier, prepared to launch a denial-of-service assault, spam your inbox, or do anything the bot herder instructs. These, and many other types of malware, are all protected by a decent antivirus.
In theory, you can set up your antivirus protection and forget about it, allowing it to buzz along in the background, download updates, etc. In practice, you should review it regularly. Most antivirus software programs display a green banner or icon when everything is in order and your data protection is active. If you launch the program and notice yellow or red, follow the on-screen instructions to restore the order.

Make sure you’re aware of the privacy policies.
Do you remember those huge chunks of text you have to wade through and “accept” before you can use that new app that converts your photo into a grandmother or tells you which dog breed to adopt? Well, here’s some bad news: you should be reading them. We know that we’ve all become desensitized to the point where we click through as quickly as possible. According to research, only 9% of Americans check privacy settings. However, we must understand how and why our data may be used to make smart choices about how we secure ourselves online.

For each login, use a different password.
Getting a bunch of user credential combinations from one place and repeating those same combinations everywhere is one of the quickest ways for hackers to access data. Let’s imagine thieves hacked an email provider and obtained your user credentials. They might try to get into financial websites or large online retailers with the same credentials. The single most effective strategy to stop a data breach from spreading is to establish a strong, distinctive password for every digital account you have. A human being can’t create a new and strong password for each account. That‘s where you need your password manager’s built-in unique password generator.
There are several helpful free password managers available, and starting up with one only requires a few minutes. Password managers that are paid for, on the other hand, usually have more features. The only password you ought to memorize when using password management is the main password that unlocks the password manager. When you enter the password manager, it instantly connects you to your online accounts. Not only will you be safer, but you will also be more efficient and productive. You won’t have to waste time inputting passwords or deal with the hassle of resetting a forgotten one.

What are the hallmarks of a phishing scam?
If you’re unable to recognize the red flags connected with possible online risks, all of your digital readiness will be for naught. Phishing schemes are the most prevalent way for our online privacy to be abused and our data to be taken. With 214,324 recorded intrusions from 2019 to 2020, the number of these cyberattacks has increased dramatically. But exactly what is phishing? Simply stated, a phishing scam involves sending an email or text message that appears to come from a reputable source, like a bank or phone company, to acquire sensitive personal data. Here are some things to keep an eye out for:
✅ Although the message claims to be from a company, it is sent from a public email address.
✅ A notice telling you that your account has been banned or that you must click on a link to modify your account protection details.
✅ Misspelled words and grammatical errors: genuine organizations’ correspondence will rarely contain obvious spelling errors or grammatical mistakes.
✅ Deals that appear too good to be true. Remember Grandma’s advice: if something seems too good to be true, it probably is.
✅ Messages aimed at instilling a sense of emergency. If your bank informs you that you need to “act immediately or your account will be permanently locked” or that you’ll “lose out on a one-time offer,” these are both warning signals.

Beware of public Wi-Fi
It’s recommended to resist accessing public Wi-Fi if at all feasible. Why? Hackers can easily access your data and gadgets when you use public Wi-Fi. So the next time you need to write a quick email using your laptop, you might be better off using your smartphone to set up a hotspot rather than connecting to an unprotected Wi-Fi network nearby. Public networks should be avoided, even if they appear to be affiliated with legal organizations. “Starbucks Public Wi-Fi #12” can be the name of anyone’s network. If you’re using public Wi-Fi, try to avoid logging into any application or website that has sensitive data about you, like banking or health records. If you are not using Wi-Fi, turn it off. This way, your smartphone won’t connect to a suspicious hacker’s Wi-Fi network by accident.
You should also install a virtual private network (VPN). A virtual private network (VPN) is a fantastic solution to secure your privacy online, both at home and when using public Wi-Fi. A Virtual Private Network (VPN) does what it says: it creates a private work connection that hides your IP address and makes it impossible to track you down. This may seem a little like a “spy movie,” but believe us when we say that it means privacy for you and your personal information.

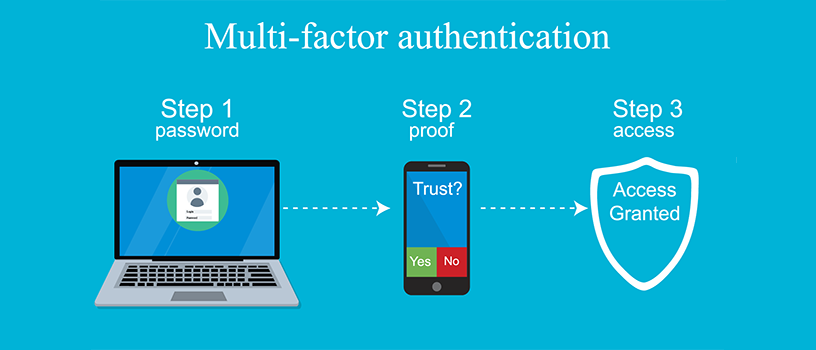
Use Multi-factor Authentication
Multi-factor authentication is tedious, but it ensures that your accounts are secure. To gain access to your accounts, you must first pass the second tier of authentication, in addition to your login and password. You should set up multi-factor authentication if the contents or personal details in an account are important or sensitive and the account allows it. Multi-factor authentication is available in several online applications, including Gmail, Evernote, and Dropbox. Multi-factor authentication confirms your identity by using at least two types of verification: who you are, what you have, and what you know. The password is something you already know. Something you could refer to as fingerprints or facial recognition verification. Something that you have might be your smartphone. You might be prompted to SMS a code or press a verification button on a mobile app to authenticate your identity.
A physical security key, for example, could be something you have; Google and Microsoft have both stated that this type of authentication is on the rise. If you rely solely on a password for security, anyone who discovers it has access to your account. Passwords are no longer sufficient when multi-factor authentication is activated. Multi-factor authentication is supported by most password managers, while some only demand it when a connection from a new device is detected. Multi-factor authentication must be enabled for your password manager.
Conclusion
Many measures can be taken to keep your information and personal data safe and out of fraudsters’ hands. Data protection and privacy need continuous maintenance, but trust us when we say that the peace of mind that comes with knowing your data is safe is well worth the time and effort.
Tags: Data, Data Protection, Data Protection Online, Data Security, Online Data Protection, Social Media, Web
